
Cryptanalysis and improvement of the YAK protocol with formal security proof and security verification via Scyther - Mohammad - 2020 - International Journal of Communication Systems - Wiley Online Library

An online security protocol for NFC payment: Formally analyzed by the scyther tool | Semantic Scholar

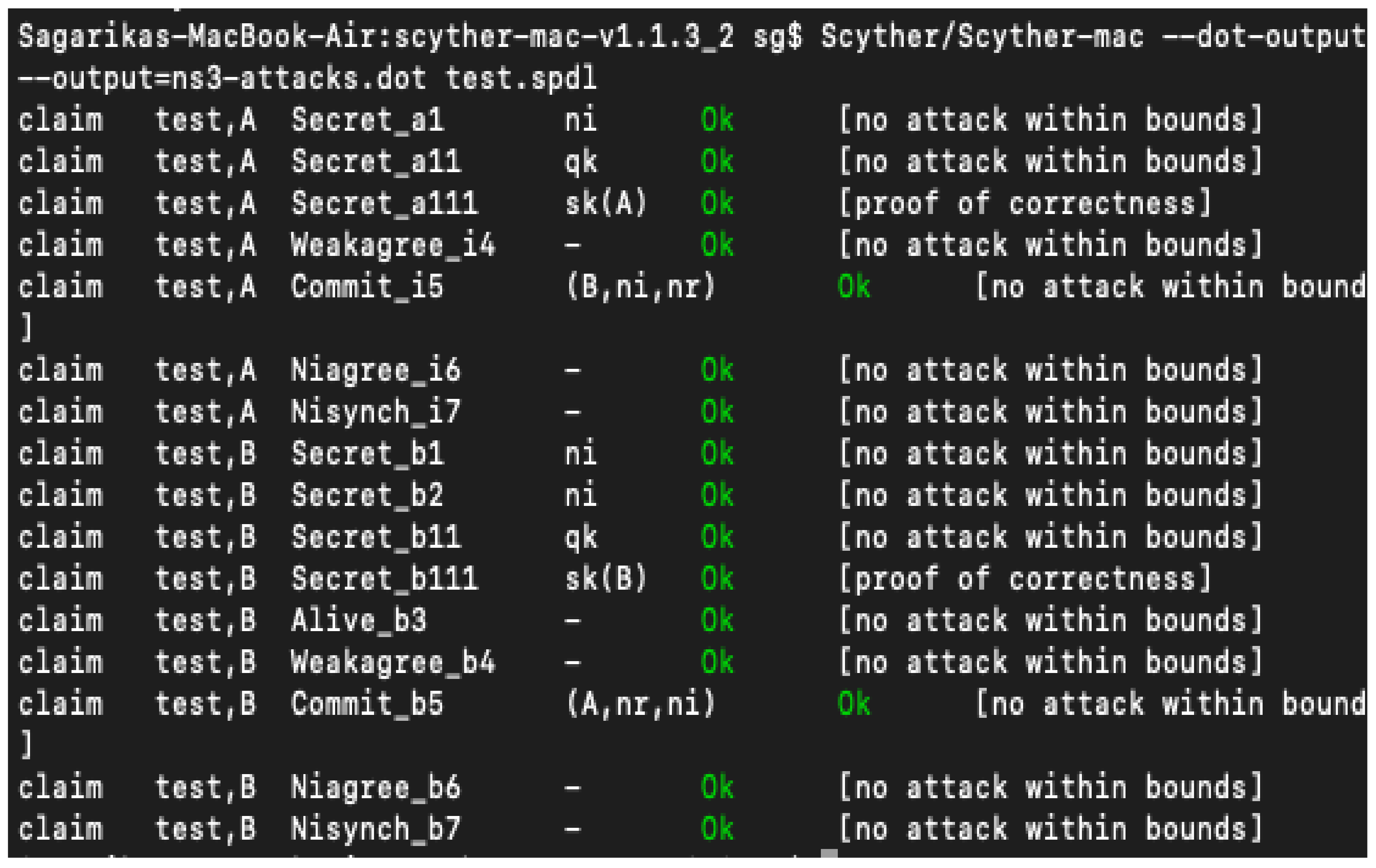
Result using 'automatic claim' procedure in Scyther tool (see online... | Download Scientific Diagram
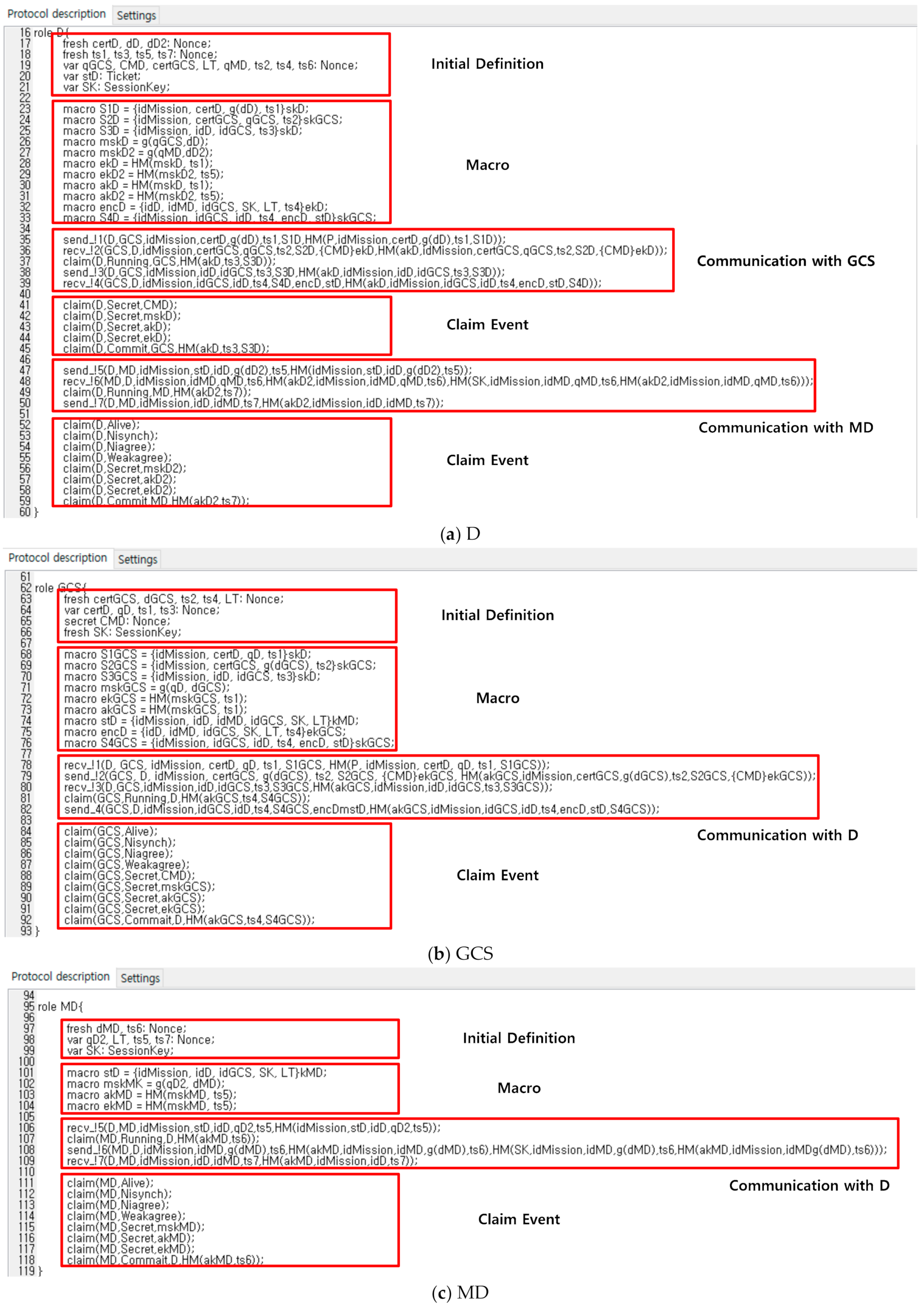
Sensors | Free Full-Text | Drone Secure Communication Protocol for Future Sensitive Applications in Military Zone | HTML

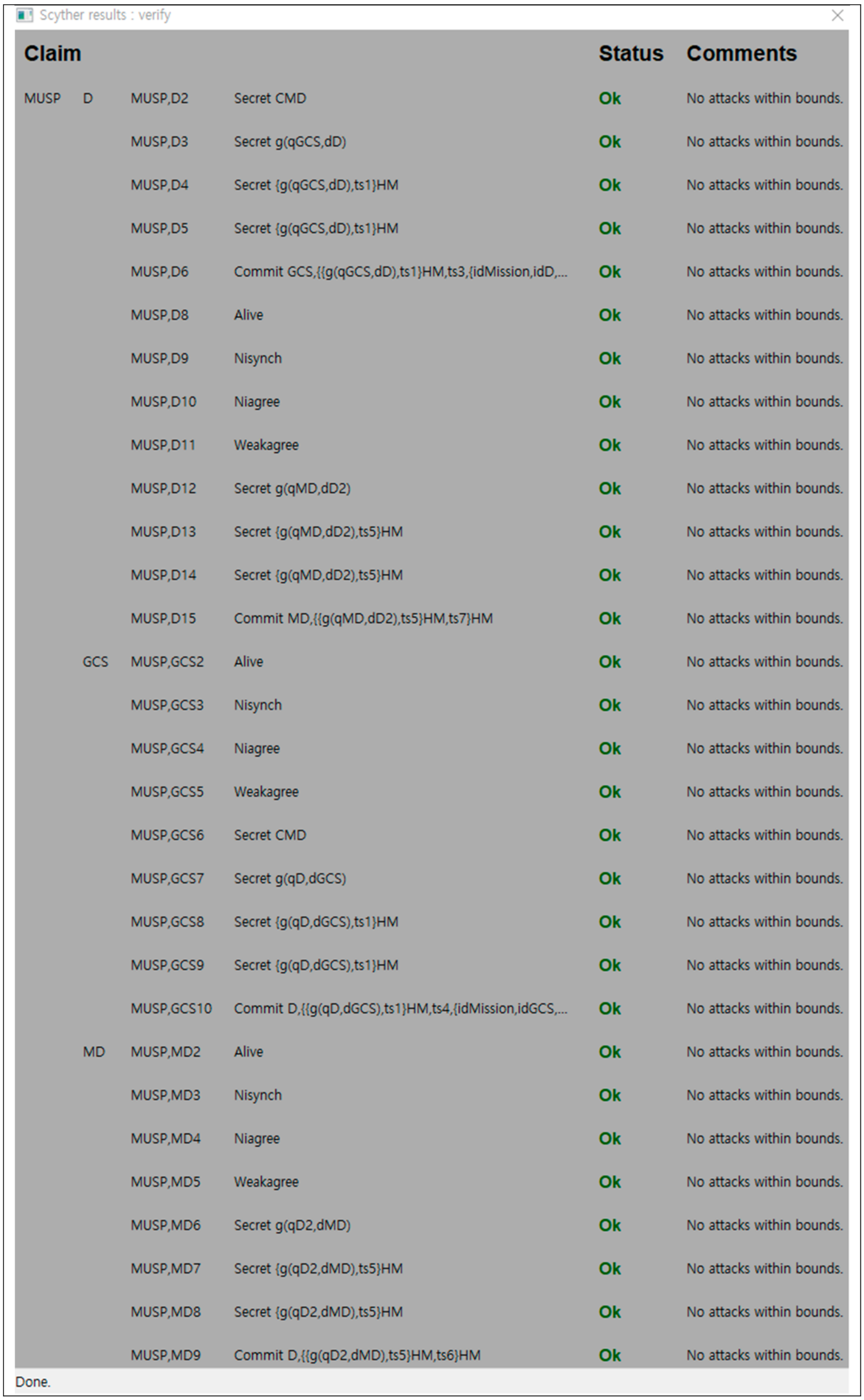
The results using 'verification claim' procedure in Scyther tool (see... | Download Scientific Diagram

The results using 'verification claim' procedure in Scyther tool (see... | Download Scientific Diagram
Applied Sciences | Free Full-Text | An Intrusion Resistant SCADA Framework Based on Quantum and Post-Quantum Scheme | HTML

On the designing a secure biometric-based remote patient authentication scheme for mobile healthcare environments | SpringerLink

The results using 'verification claim' procedure in Scyther tool (see... | Download Scientific Diagram

Analysis and improvement of the Internet‐Draft IKEv3 protocol - Cheng - 2017 - International Journal of Communication Systems - Wiley Online Library

The results using 'verification claim' procedure in Scyther tool (see... | Download Scientific Diagram








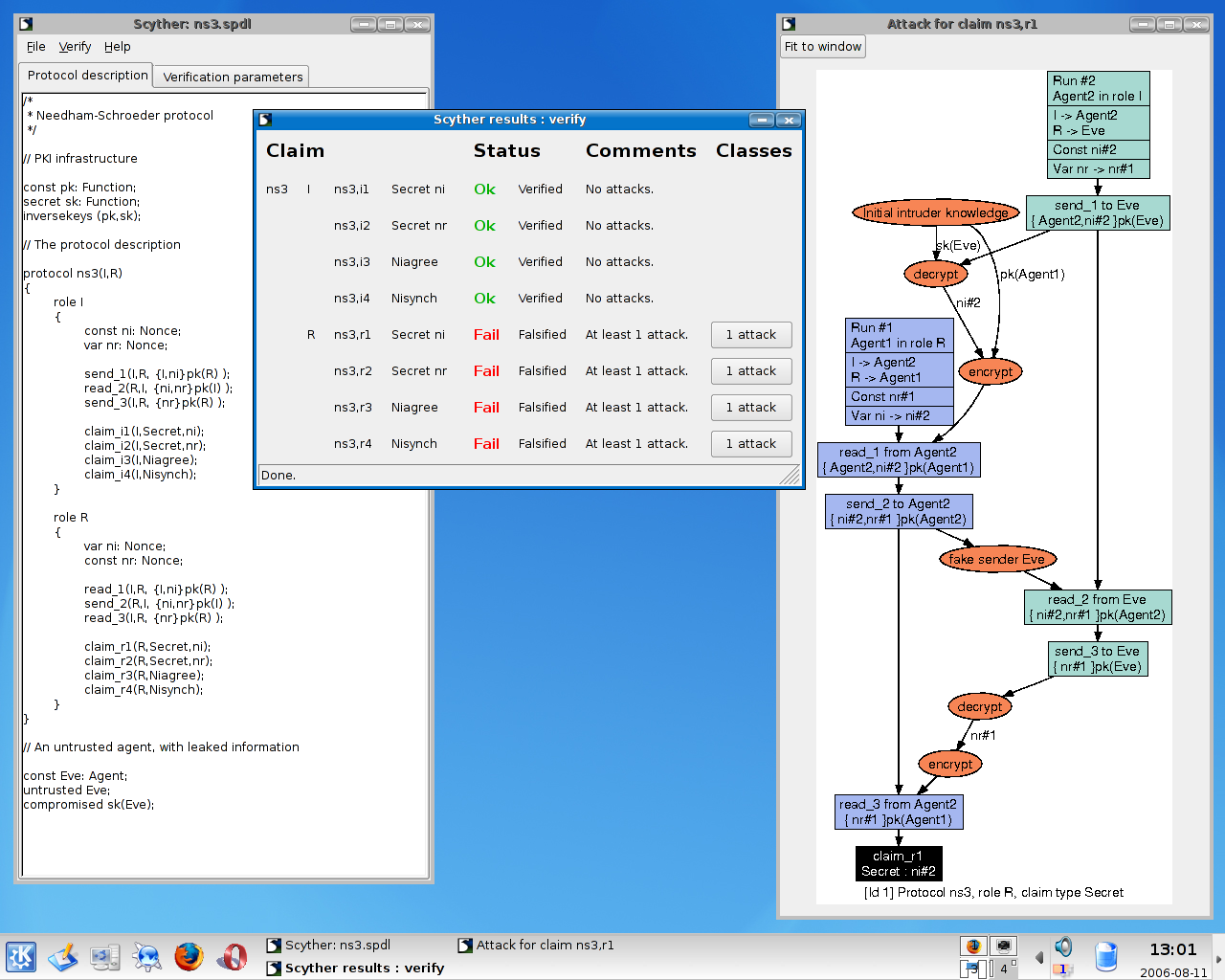
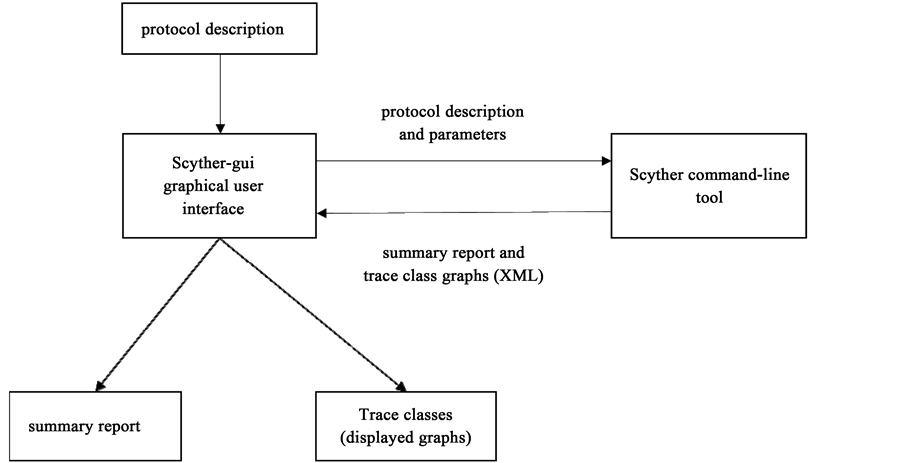


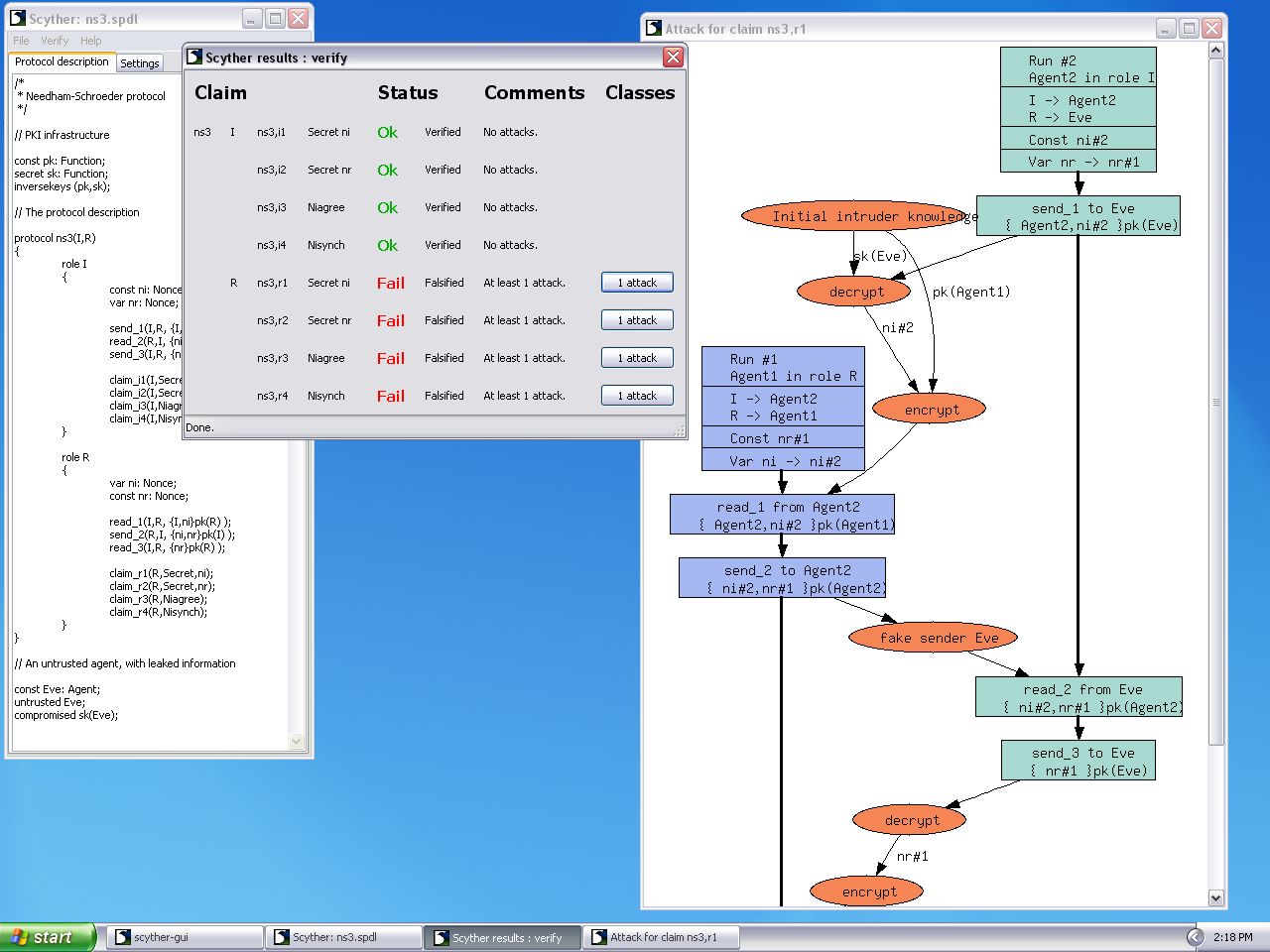
![PDF] Verifying Group Authentication Protocols by Scyther | Semantic Scholar PDF] Verifying Group Authentication Protocols by Scyther | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/afecefc52bb5c36f7b968eac7aaf7c24361b5813/12-Figure3-1.png)